Use Systems Manager Session Manager with Stax Networks VPCs
When you create VPCs with Stax Networks there are a few tasks you'll need to complete before you're able to use AWS Systems Manager Session Manager with instances inside these VPCs. You must configure the proper IAM Instance Profile, create S3 endpoints in your VPCs, and configure the appropriate Security Group for your instances.
If you're not using Stax Networks, see Use Systems Manager Session Manager.
Before You Begin
- Estimated time to complete: 15 minutes
Why do I need to do this?
When you use AWS Systems Manager Session Manager, it requires access to trigger messages to the Systems Manager control plane, and also to write logs to an S3 bucket. This access requires an appropriately configured IAM Instance Profile, VPC endpoints to be created, and a correctly configured Security Group.
Configure the Security Group
For AWS Systems Manager Session Manager to function, your instance will need a Security Group rule permitting it access to the Systems Manager control plane. The default rule of 0.0.0.0/0 to any is sufficient for this.
Configure the IAM Instance Profile
Your instance(s) will need an IAM Instance Profile assigned that permits the Systems Manager activities that are required. The easiest way to do this is to apply the AmazonSSMManagedInstanceCore managed policy to your Instance Profile. Additionally, you'll require a policy or in-line policy that grants the instance access to write to the Stax Session Manager logging bucket:
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:PutObjectAcl",
"s3:PutObjectTagging",
"s3:GetEncryptionConfiguration",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::<SMSM_BUCKET_NAME>",
"arn:aws:s3:::<SMSM_BUCKET_NAME>/*"
]
}
In the JSON policy syntax above, replace the <SMSM_BUCKET_NAME> placeholder with your AWS Systems Manager Session Manager S3 bucket. This bucket resides in your Logging Account and will have a name similar to stax-session-manager-25d515d9-92d3-4ce7-8519-9c305490b5c0.
Create the S3 Endpoint
Create the Endpoints at VPC Creation Time
When you are creating your VPC you can specify the endpoints to create.
-
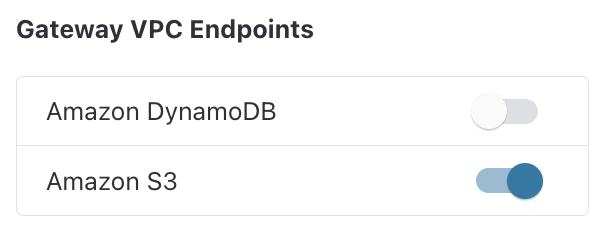
On the Create a VPC page, within the Gateway VPC Endpoints section, select Amazon S3 to create the Amazon S3 Gateway endpoint
Continue creating your VPC as per the established guidance.
Create the Endpoints for an existing VPC
If you already have an existing VPC, you will need to add the endpoints to it.
-
Follow the steps in Manage VPCs to access the VPC's configuration
-
Within the Gateway VPC Endpoints section, select Amazon S3 to create the Amazon S3 Gateway endpoint
-
Click Save to initiate the endpoint creation
Once you have configured the Security Group for the instance, assigned it an IAM Instance Profile with the appropriate permissions, and created the S3 Gateway endpoint in your VPC, you will be able to interact with your instances using AWS Systems Manager Session Manager.