Configure Google Workspace for Single Sign On
Stax integrates with your corporate identity using SAML. This allows you to bring your own identities and identity management controls to the Stax platform. Stax supports Google Workspace's cloud-hosted identity solution. It supports integration with applications as a SAML identity provider (IdP) and is available for use by organizations with a Google Workspace environment.
Before You Begin
- Estimated time to complete: 1 hour
- Ensure you are a member of the Admin role in Stax
- You need to be a super administrator of your Google Workspace
Prepare the SAML Service URIs
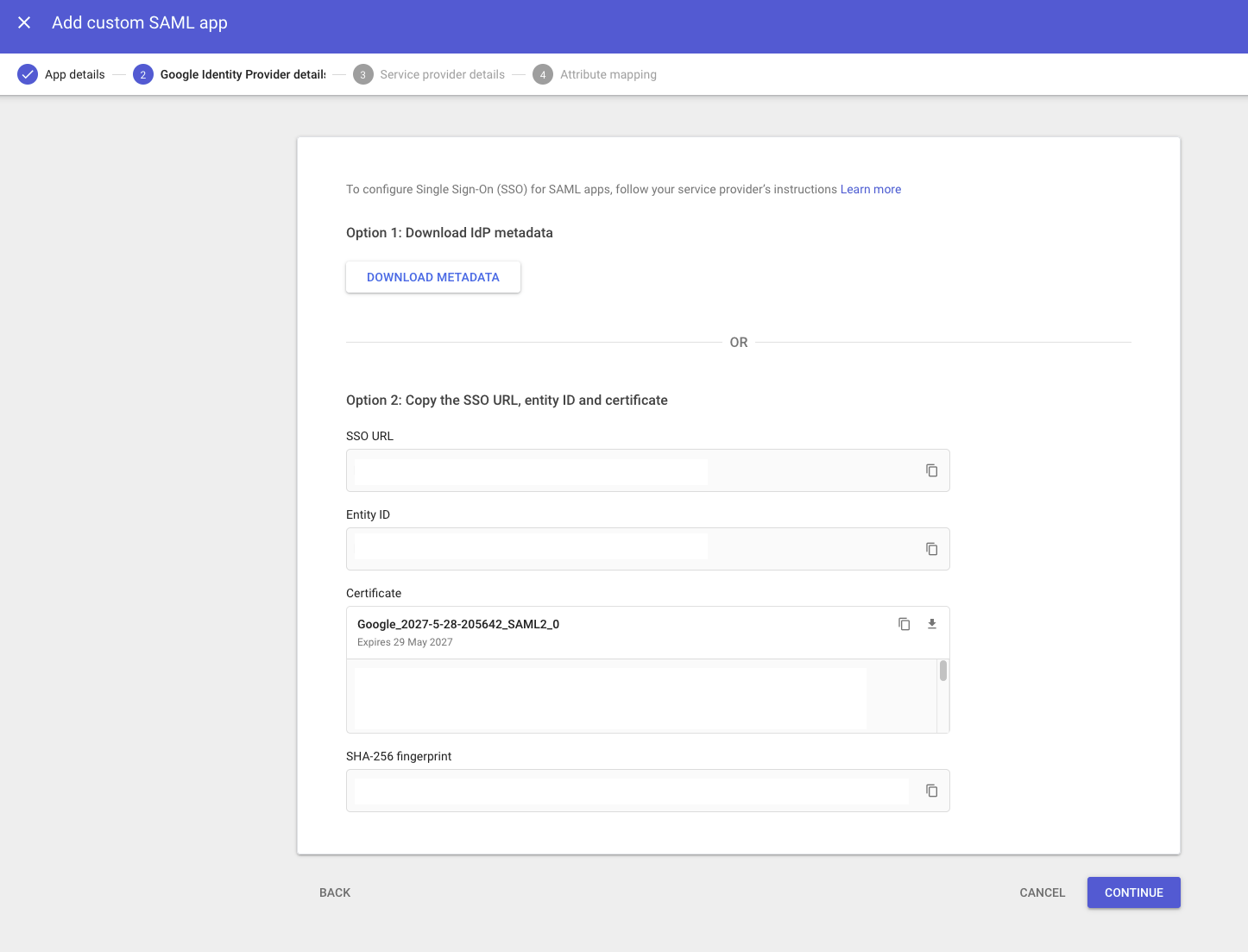
Determine your SAML Service URIs (Entity ID and SAML 2.0 Service URL) using the guidance in Configure Single Sign-On.
Create a custom attribute for Stax Role
Stax requires an additional attribute to be created in your environment for the purpose of recording users' role in Stax. This role must be created before you can configure SSO.
-
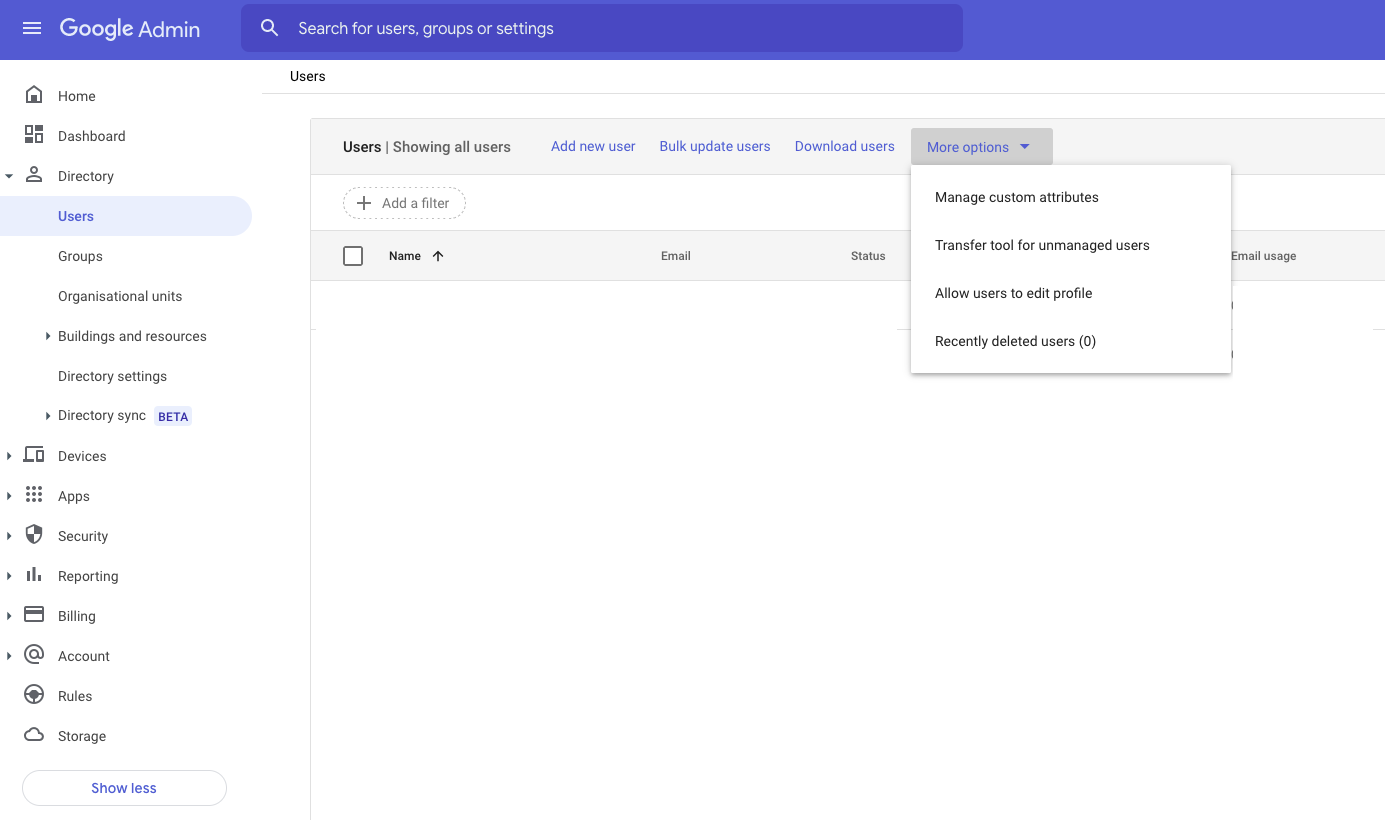
Log in to the Google Admin console
-
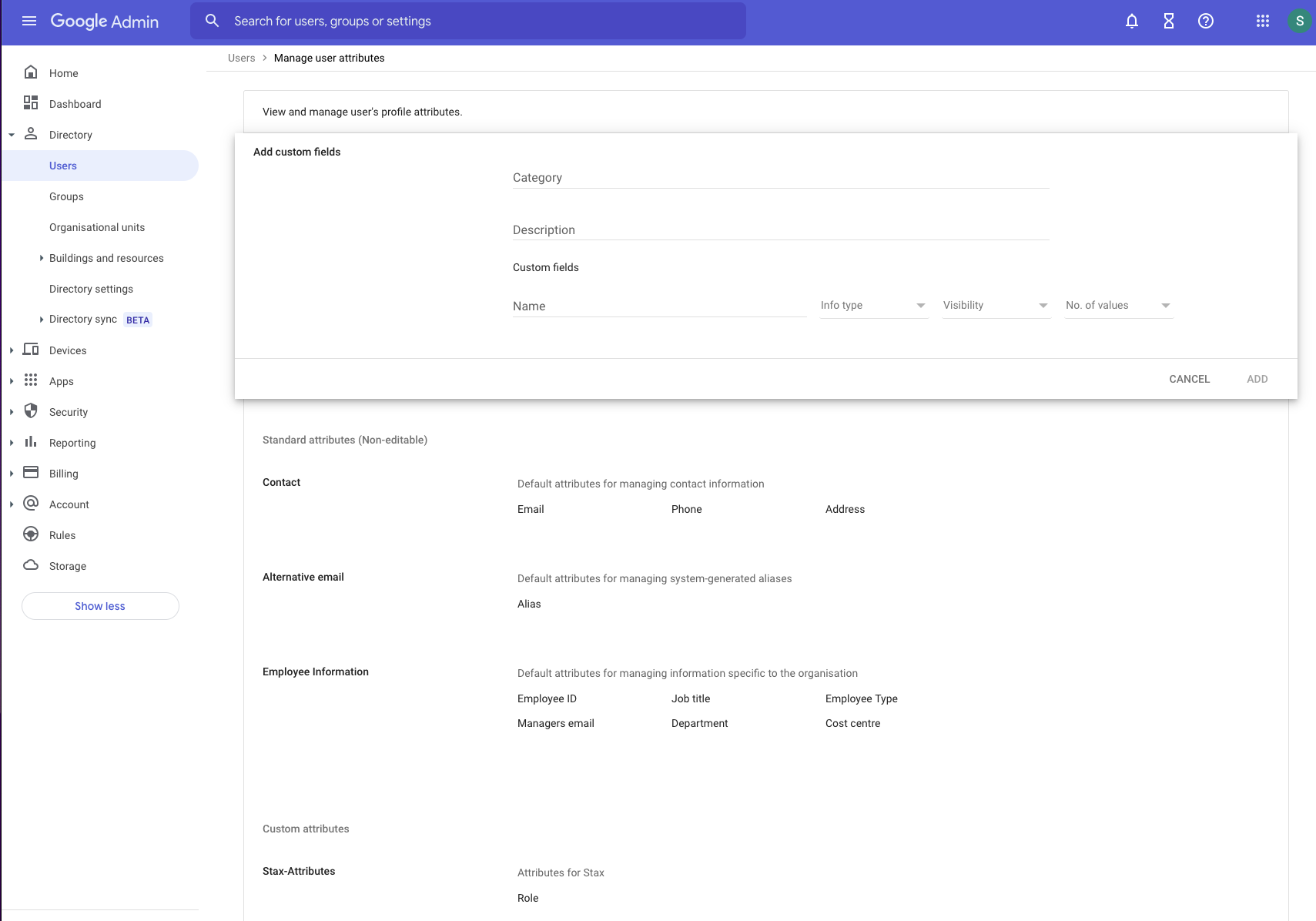
From the left-hand nav, choose *Directory,*then Users. On the Users screen, choose More Options then Manage Custom Attributes
-
Choose Add Custom Attribute and create the following attribute. Once complete, click Save
Category Name Info Type Visibility No. of Values Stax Role Text Visible to Organization Single Value
Create the SAML app
-
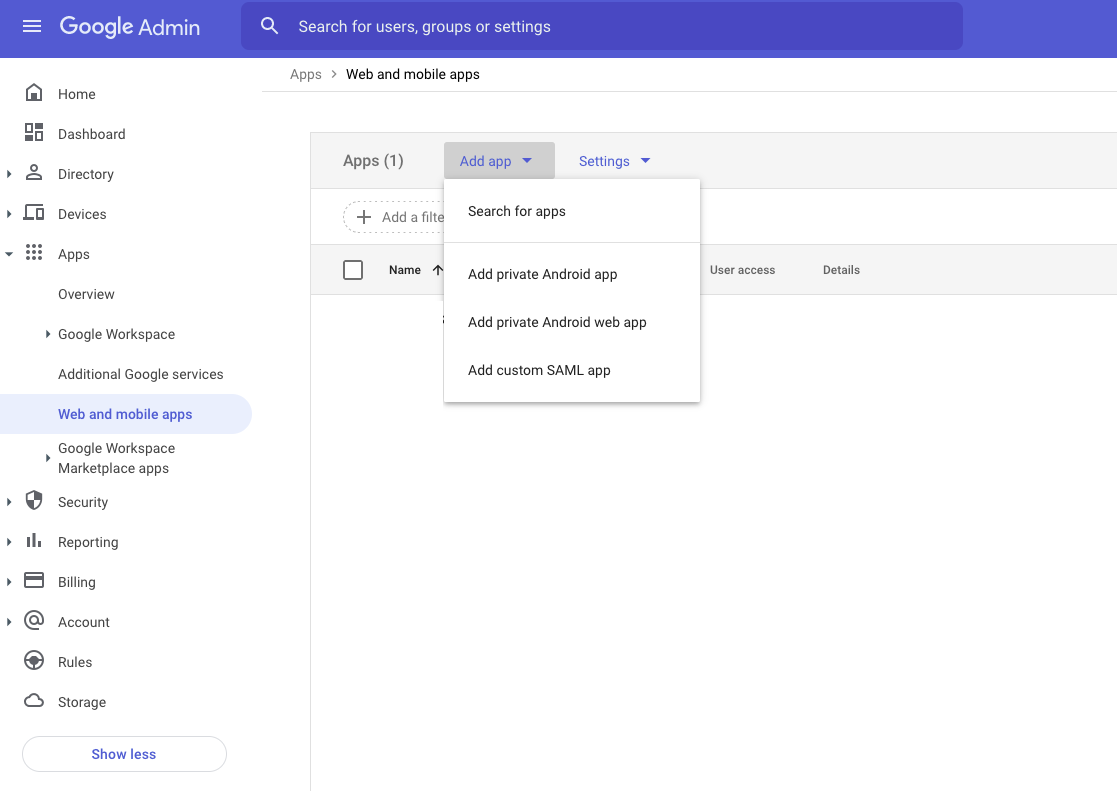
Log in to the Google Admin console
-
From the left-hand nav, choose Apps then Web and Mobile apps
-
On the Web and mobile apps page, choose Add App then Add custom SAML app
-
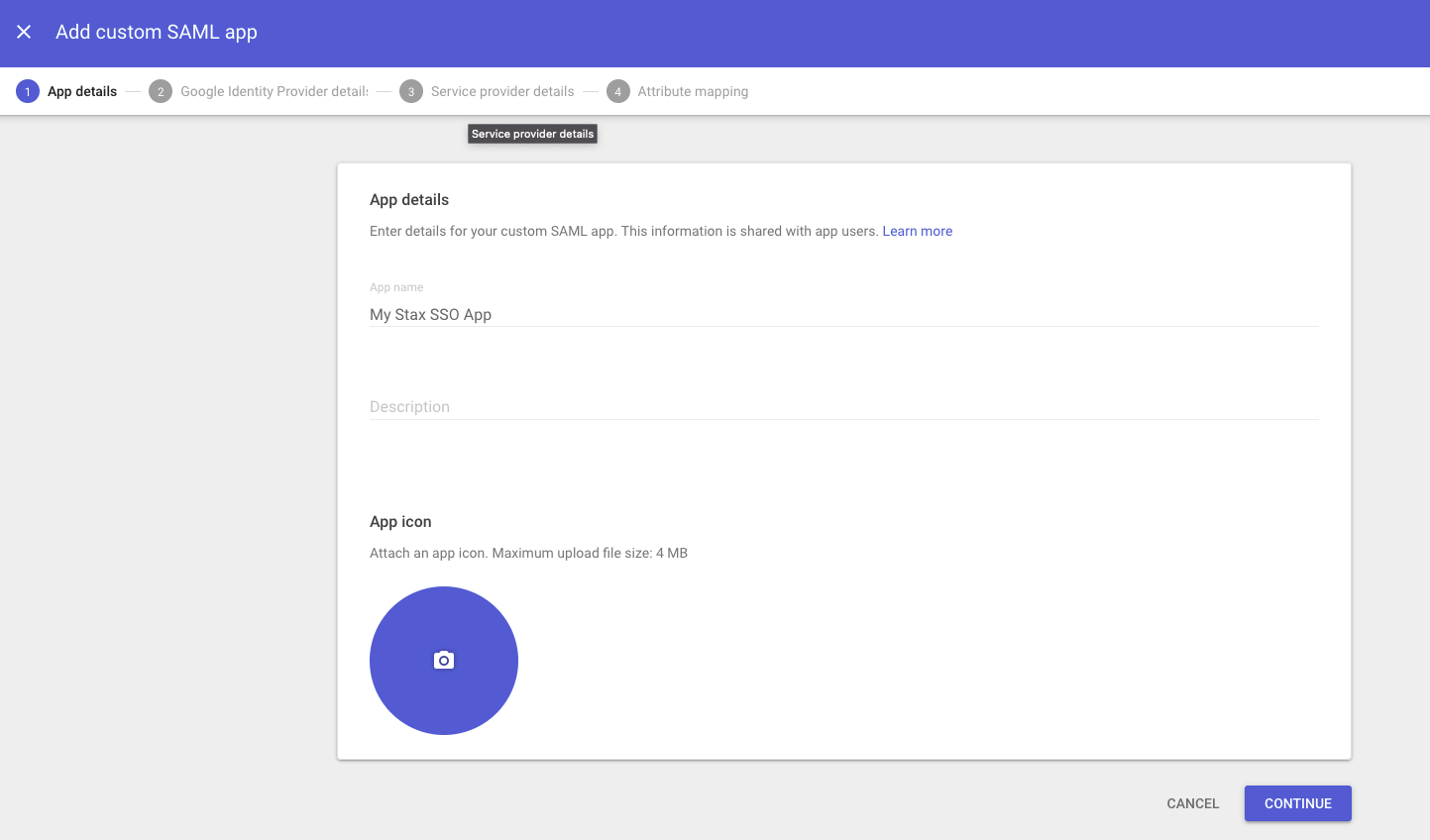
Name your application appropriately (for example, simply Stax)
-
Choose Download Metadata to download the SAML federation metadata. You'll need to provide this to Stax later
-
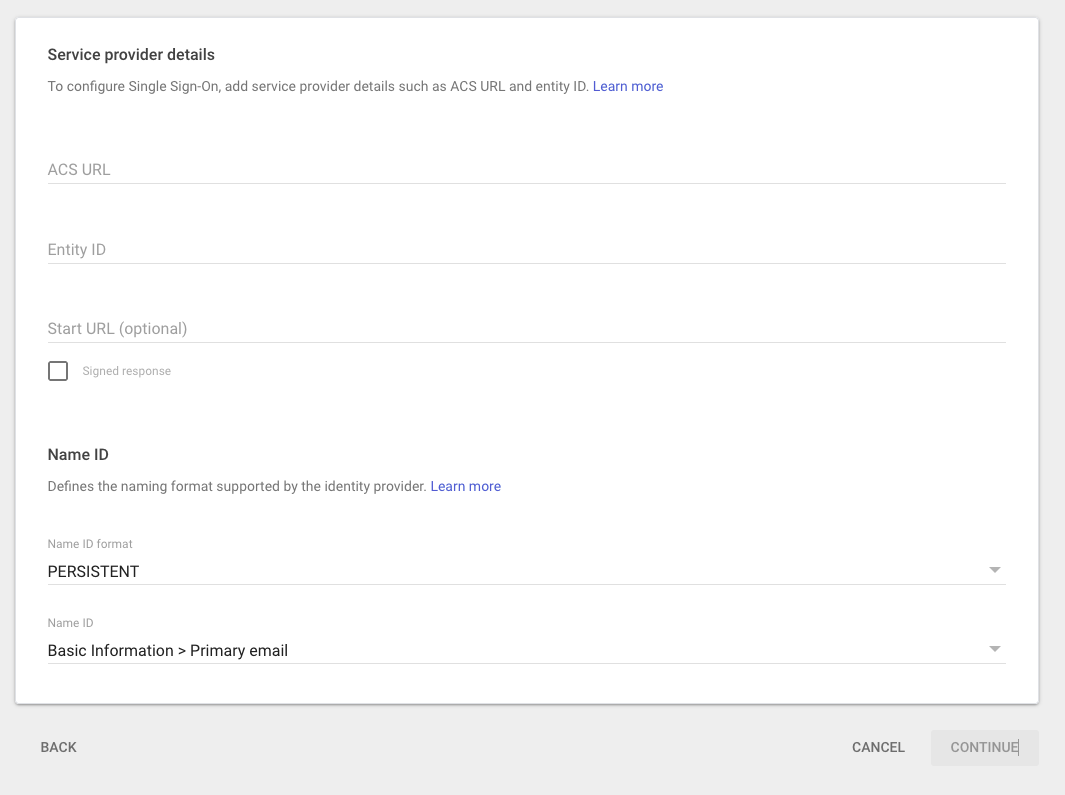
Input the Service provider details:
Parameter Value Example ACS Url The SAML 2.0 Service URL you determined earlier https://id.security.mega-corp.au1.staxapp.cloud/auth/realms/master/broker/saml/endpoint Entity ID The entity ID you determined earlier https://id.security.mega-corp.au1.staxapp.cloud/auth/realms/master Name ID Format PERSISTENT Name ID Basic Information > Primary Email -
Once completed, choose Continue
-
Configure the attributes as per the Configure Single Sign-on page.
Google Directory Attribute App Attribute First Name firstName Last Name lastName Primary email email Role Role
Configure Stax to allow SAML Sign In
When you're ready to have Stax configured, you will need to raise a support case with your SAML metadata file and the ACS URL of your SAML IdP. Once SAML is configured for your Stax tenancy, the support team will be in touch to let you know that it's ready to be tested.
If you encounter issues when configuring single sign on with Google, you may need to re-download the Google metadata file again.
How do you know this worked?
At this time, Stax does not support IdP-initiated sign-ins. You must use SP-initiated sign-in to access Stax.
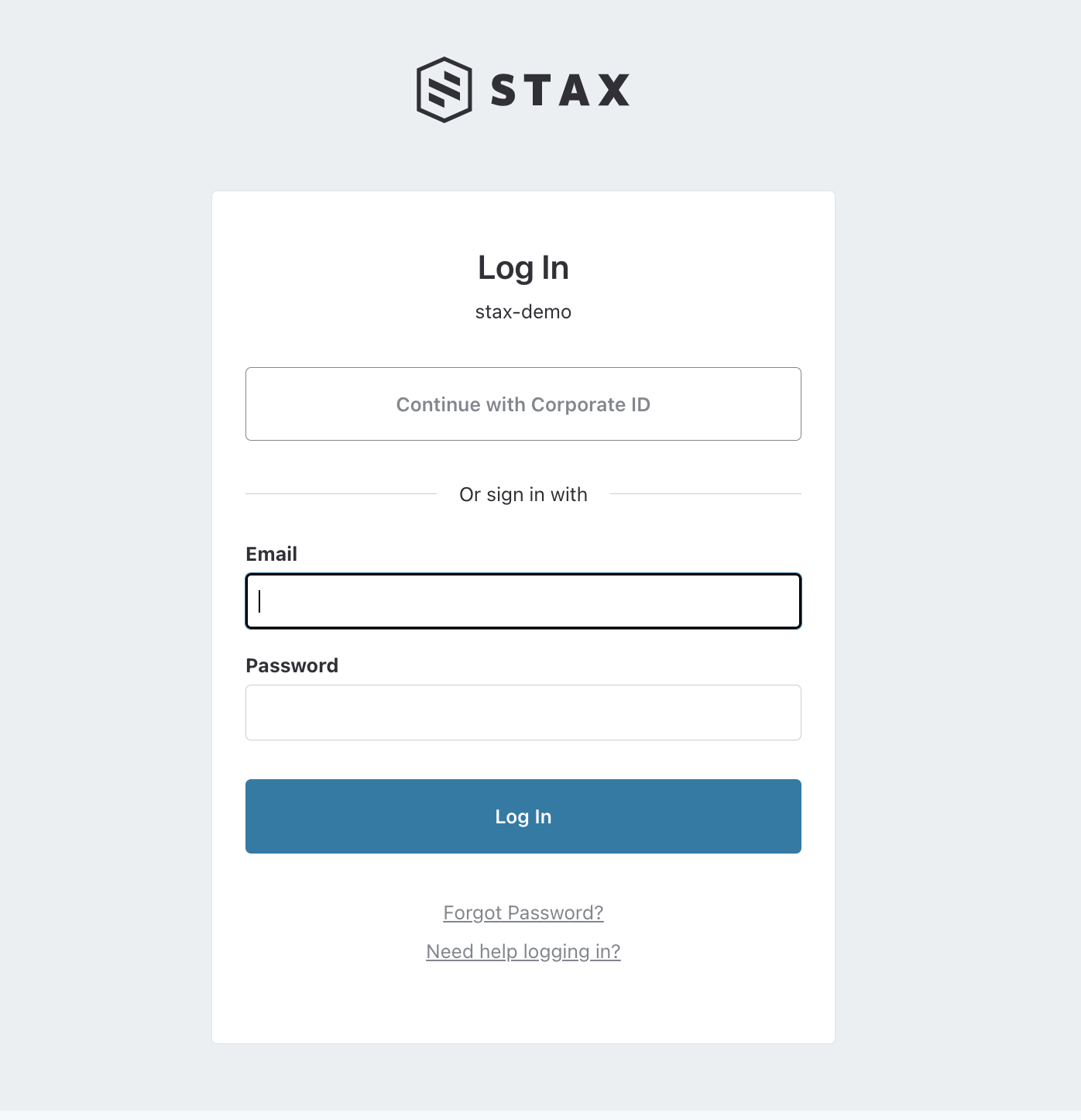
Next time you navigate to your Stax Console login page, on the top, you'll see a new Continue with Corporate ID button. Clicking this button will take you to your SAML sign-in page. Log in to the IdP and you'll be signed into your Stax tenancy.